If you were browsing the LinkedIn job boards this morning, you could have come across a job opening from Mashable titled “Assistant to Matt Binder.”
Even though it appears right there on Mashable’s official LinkedIn business page, the company, unfortunately, is not hiring me an assistant. Mashable’s human resources department did not post that job listing. No one at the company posted the opening. The job does not exist.
So, how did it show up alongside the company’s very real, official job posts?
Rijnders discovered a serious flaw embedded within a very basic LinkedIn feature that allows users to post an official looking job opening on nearly any company’s LinkedIn business page. These unofficial listings show up on a company’s “Jobs” page and look just like any other job opening posted legitimately by the organization.
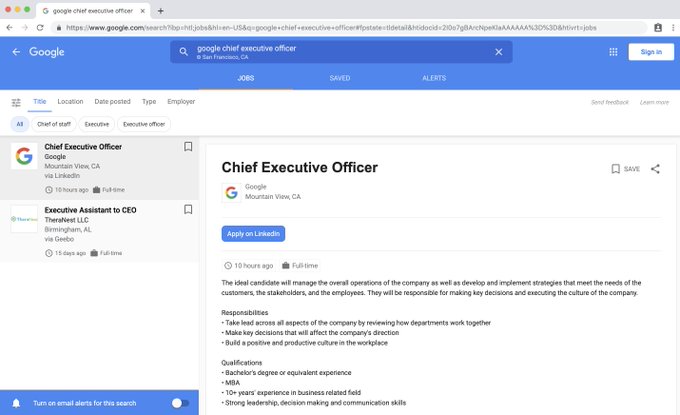
Earlier, Rijnders created job posts for a new Chief Executive Officer for LinkedIn and Google, something he very much has zero authority to do. Both fake listings appeared on the tech giants’ LinkedIn business pages alongside their other job openings. The listings also appeared in LinkedIn’s job search. There was no approval process required.
While LinkedIn does usually charge for posting a job listing, Rijnders, a premium LinkedIn subscriber, says he has been able to list each job opening for free.
LOL. Never thought of the fact that the LinkedIn loophole would also make my jobpost for CEO of Google appear on Google Jobs. twitter.com/parthi_logan/s…
Google, which scrapes hirings from recruitment websites all over the internet, aggregated the fake opening for its CEO position to its own job platform. Sorry, actual Google CEO Sundar Pichai.
Rijnders was even able to take LinkedIn users offsite by linking his own business’ website to the “Apply” button on the job listing.
It’s easy to see how a scammer could use these fake but official-looking listings, aggregated all over the web to other trusted sources who also believe the listings to be official, for nefarious means. People hand over a lot of personal data when applying for a job.
In fact, one notable offender, a job-scraping site called Jooble, is what tipped off Rijnders to the problem to begin with.
“For a while I noticed scrapers, like Jooble, posting massive amounts of jobs at companies on LinkedIn without consent of those companies,” wrote Rijnders in an email to Mashable. “A lot of companies complained without any result. The bad thing is [the scrapers] collect the application details of applicants who think they actually apply at the company. These companies also seem to only pick smaller companies to do this with less risk of getting into trouble.”
Other LinkedIn users replied to Rijnders’ LinkedIn post saying that they’ve brought up this problem to the company before.
SEE ALSO: LinkedIn is full of spies
“Because LinkedIn didn't really seem to see this as a problem, I used the same loophole to make the problem a bit more clear and urgent to them,” he explained. “That worked.”
LinkedIn is now apparently aware of the issue.
“Thank you, Michel Rijnders, for bringing this to our attention,” wrote LinkedIn’s head of trust and safety, Paul Rockwell, in a comment under Rijnders’ post. “We've removed the posting and we're resolving the issue that allowed this post to go live.”
“LinkedIn is a place for real people to have real conversations about their careers. It's not a place for fake jobs,” Rockwell continued. “Posting jobs without explicit permission or knowledge of another party is against our Terms of Service. We are committed to stopping fraudulent jobs from ever reaching our members through automated technology and the help of our members reporting any suspicious job postings.”
While Rijnders confirms that his fake LinkedIn and Google listings were removed by the company, he was still able to exploit the flaw to create a Mashable listing more than 24 hours after publishing his post.
UPDATE: July 26, 2019, 5:01 p.m. EDT In addition to the earlier comment from LinkedIn's head of trust and safety, Paul Rockwell, a company spokesperson sent us the following statement:
This issue was caused by a bug in our online jobs experience that allowed members to edit the company after a job had already been posted. The issue has now been resolved.
Fraudulent job postings are a clear violation of our Terms of Service. When they are brought to our attention, we quickly move to take them down.
While we do allow companies to post on behalf of other companies (such as in the case of recruiting firms), this is only permitted with the knowledge of both parties.
Regarding free job postings, we have not historically had free job postings as part of the LinkedIn experience. However, we’re running a test that allows small and medium sized businesses to post a limited number of jobs for free. This member was a part of that test.









No comments:
Post a Comment